I have wanted to learn how to verify with software for a while because I have a habit of erasing my laptop from time to time, and I need to make sure I'm backing up EVERYTHING since I'm often on the road exploring—if anything happens, that might be lead to many problems, but I'm the one to be blamed; For example, I had forgotten to backup some articles before, and they are gone, so I need to make sure I'm more antifragile by constantly testing my own backup with erasing.
The second reason is when you are around Bitcoiners so much with all the verifying, you really want to make sure all the software you use is genuine. Also, I've stopped using the Apple Store for a while, downloading software from sites could be risky, even though I do verify the URLs, but you never know! So one of the to-does for me is to learn how to verify software because I need to download it every time. I shared some of the questions I had in the saloon, and @ek patiently wrote this guide on how to verify better, so I'm writing down a more detailed article to help others who also want to learn the art of verifying. 👀
Why Verify
I'm not going to focus on the why here, but if you are a Bitcoiner, you know the why - don't trust, verify, especially with all the phishing sites and malicious software these days.
Also, if you think this is way above your head or is not for a normal person, I'm happy to tell you that I don't have any coding skills, but I'm willing to test and learn—so if I can do it, you can too!
What to Verify ( Important! )
When I started dipping my toe into verifying, I didn't know what I should verify at all. 👀 but then I read a few docs and followed some of the official guides from the software that I use, and of course, this good piece from @ek; I figured it's actually needed to verify two things when it comes to verifying software:
1. The public key, which is used to sign the software release.
When importing a public key, you should check the fingerprint to verify it's the correct public key and ideally from independent sources, and from more sources, the more trusted.
2. The signatures.
" Digital signatures are commonly used to ensure the integrity and authenticity of software. When you verify a digital signature, you make sure that the software was created by the person you trust and think it was created by (authenticity) and that it was not modified (integrity). You usually download the signature from the same location as the software. " explained by @ek
There is also a tricky part: if the signature file name (ASC) does not match the dmg file that you downloaded, you need to do one more step for the checksum verification, which verifies the hashes, and it usually shows in the site too when you need to do this step. ( unfortunately, I'm not that technical being able to explain this, feel free to chip in. )
The Setup
In order to verify, we need to install the tools first, home brew and gnupg ( Or install GPG Suite if you are also using a Mac ) but I recommend using the terminal for more solid learning.
The homebrew is quite easy to install, all you need is to put these codes into the terminal, wait a bit and done ( $ means "run this in terminal" )
1. Install homebrew
$ /bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
for better privacy enter brew analytics off
2. Install gnupg
$ brew install gnupg
that's it, you are all set! time to explore the fun. 🥁
Since I'm using a Mac, this experience is based on the Mac system; feel free to pill me other fun!
Learning by Doing
You can't learn swimming from reading, and talking is cheap; I'm going to use two of my favorite Bitcoin desktop wallets as examples for everyone to follow along and do the verification yourself.
For simplicity, we are only using a terminal as practice here.
Practice A. Electrum Wallet
Here is the guide linked to the site on how to verify:
1. Download the Software and the Signature next to it.
Be sure to put both in the same folder, e.g. in the download folder.
2. Check different sources of the fingerprint to verify the signer's public key.
In order to import from PUBLIC KEY BLOCK, run gpg --import copy the block and paste in the terminal and then CTRL+D.
And do one more step, to make sure that you imported the correct key:
$ gpg --fingerprint thomasv@electrum.org
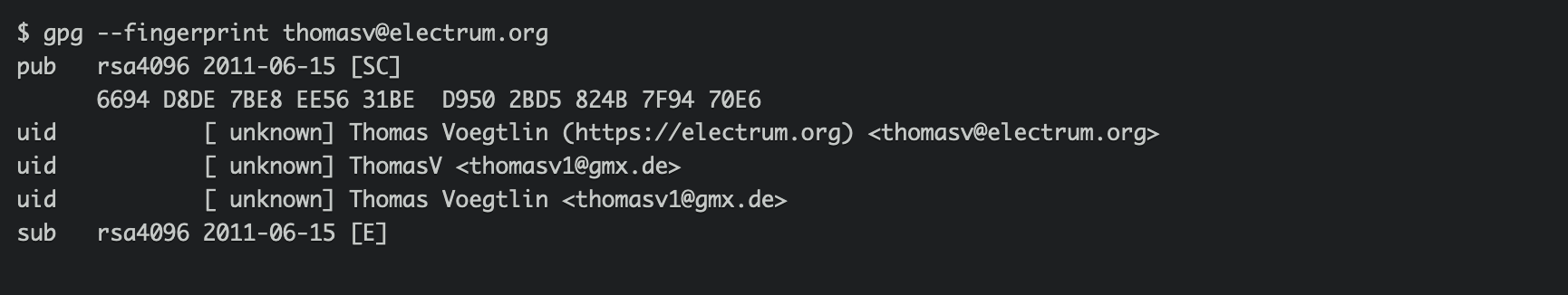
All fingerprints are matched: 6694 D8DE 7BE8 EE56 31BE D950 2BD5 824B 7F94 70E6, good!
3. Verify the signed file.
Put these two lines of code into terminal
$ cd Downloads
$ gpg --verify electrum-4.5.3.dmg.asc
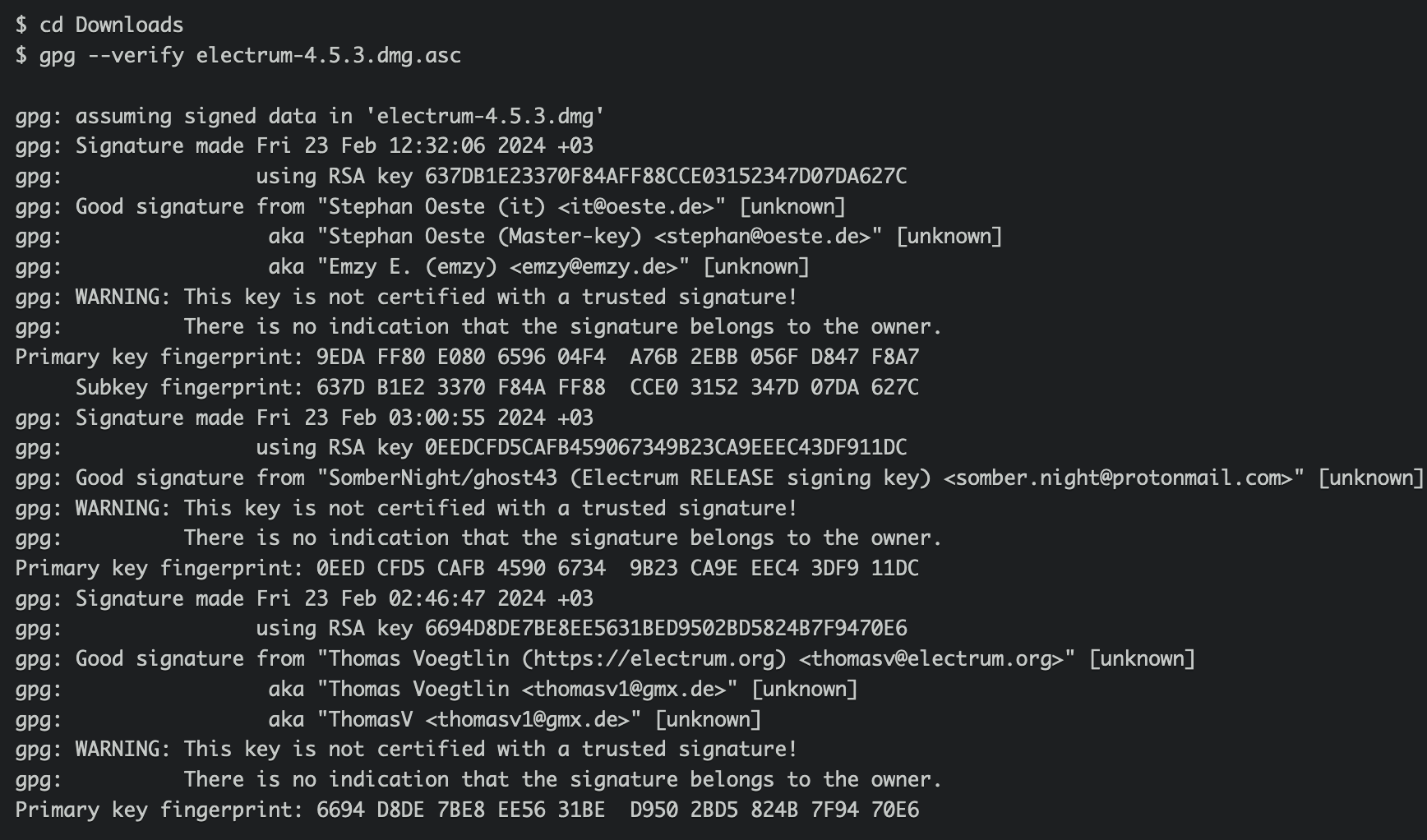
If you see " gpg: WARNING: This key is not certified with a trusted signature! " which means you didn't mark the public key as trusted, then you can run gpg --edit-key thomasv@electrum.org , enter trust and choose the numbers.
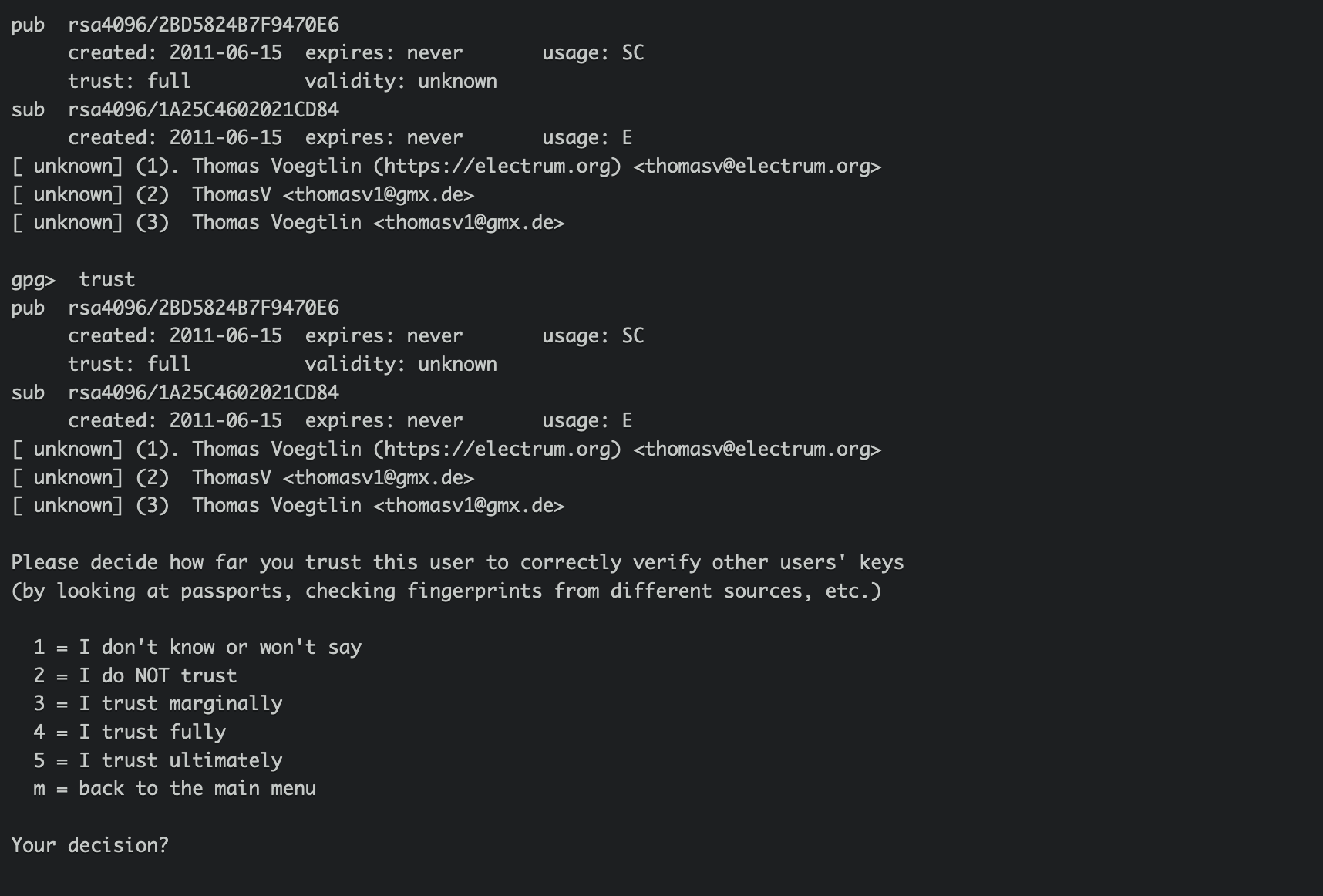
now run it again. ( And from my testing, if you want to make this warning disappear, you need to set the trust to "5 = I trust ultimately." )
And done! safe to install it now.
Practice B. Sparrow Wallet
Here is the Official guide on how to verify.
1. Download the Software, the Manifest Signature, and the Manifest next to it.
Be sure to put all the them in the same folder, e.g. in the download folder.
2. Check different sources of the fingerprint to verify the signer's public key.
And do one more step, to make sure that you imported the correct key:
$ gpg --fingerprint craig@sparrowwallet.com
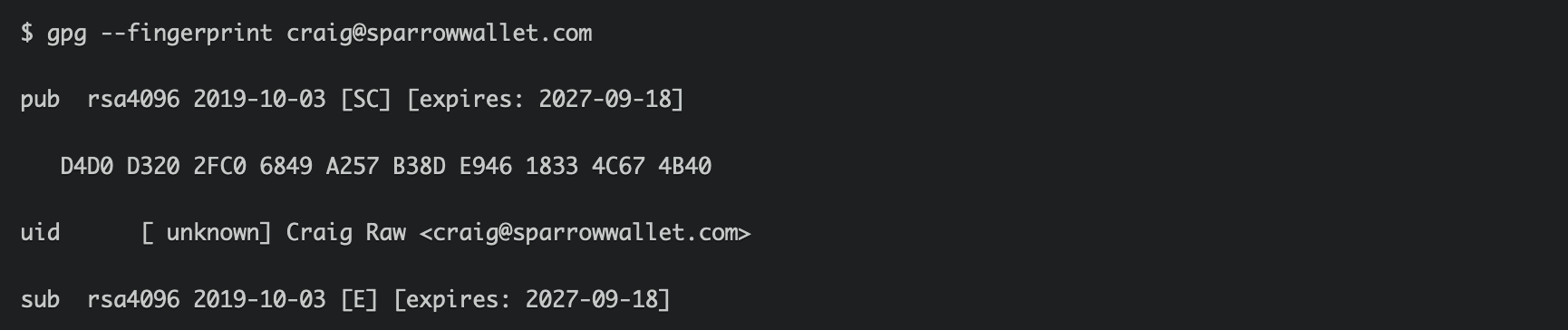
All fingerprints are matching: D4D0 D320 2FC0 6849 A257 B38D E946 1833 4C67 4B40 good!
3. Verify the signed file.
Put these two lines of code into terminal:
$ cd Downloads
$ gpg --verify sparrow-1.8.2-manifest.txt.asc
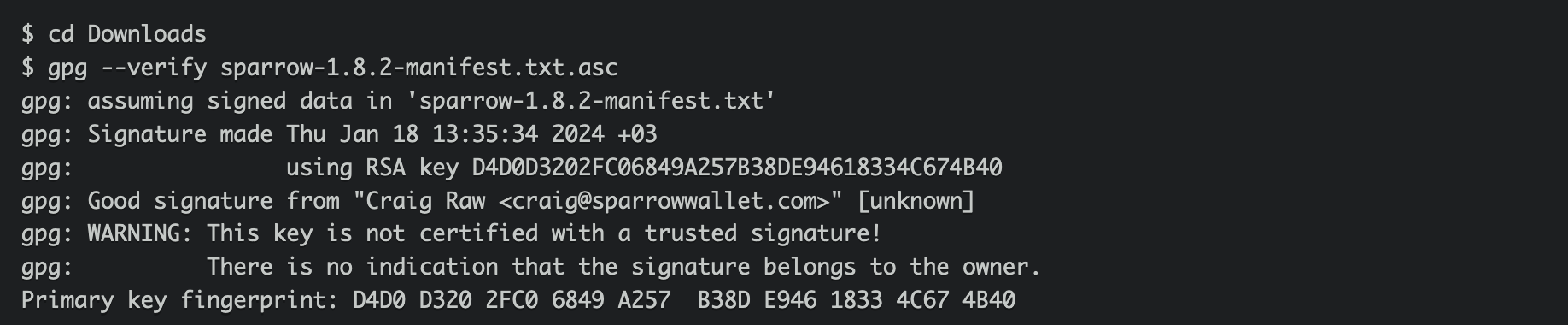
You have now verified the signature of the manifest file, which ensures integrity and authenticity of the manifest file - not the binaries!
explained by Sparrow
4. Verify the hashes.
I can see that I need to verify the hashes because the name of the signature file is different from the software, which means need to do one more step; Simply copy and paste this code into terminal: shasum --check sparrow-1.8.2-manifest.txt --ignore-missing
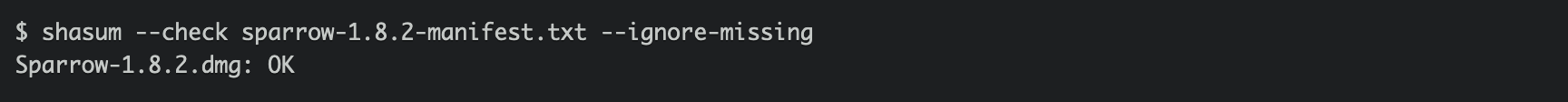
And done! safe to install it now.
🕵🏼 The Art of Verifying
1. Download the Software and the Signature next to it.
Be sure to put both in the same folder, e.g. in the download folder.
2. Check different sources of the fingerprint to verify the signer's public key.
Good places to look are Github, Keybase, KeyServer, and different socials. Generally, the more sources showing the same key, the more trusted.
3. Verify the signed file.
-- If the signature file name ( asc ) matches the dmg file that you downloaded, then run this:
$ gpg --verify {filename}.asc
-- if the signature file name ( asc ) does not match the dmg file that you downloaded, get the sha256 and additionally run this:
$ cd Downloads
$ echo "{hash} {filename}" | shasum -a 256 -c -
And congrats! now you've learned how to verify two of the best and most important Bitcoin wallets! Feel free to ask if there are anything questions or point out any mistakes, as I'm still new in this verifying, and stay tuned for more!